Unit 42 noted 2800% increase in cryptocurrency miner samples in just one year
* This is a blog post from Unit 42, research unit of Palo Alto Networks. For full review, visit the link (in English).
According to detailed analyzes of Unit 42, in January 2017, the Exploit Kit (also known by the acronym EK - malicious programs used to identify software vulnerabilities) called “Rig” was at its peak. However, in April of the same year, Palo Alto Networks research team saw a sharp drop in its use, as we can see in the chart below:
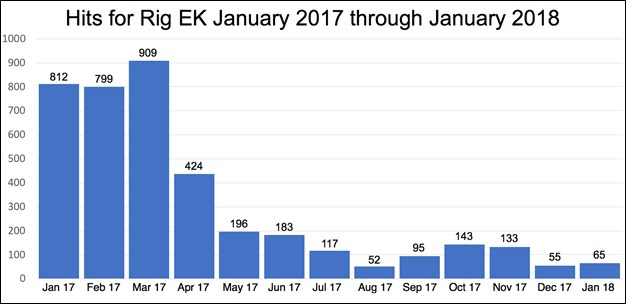
Initially, Unit 42 researchers observed this trend in the survey “Decline in Rig Exploit Kit”June 2017. Now a new survey,“Rig EK a Year Later: From Currency Mining Ransomware and Information Theft“Points out that the April 2017 decline was not an anomaly, but the beginning of a change to the Rig EK and other exploit kits as we knew them.
There are many likely reasons for this. However, as Unit 42 researcher Brad Duncan noted in June 2017 and January 2018, the likely reasons for the Rig EK decline include a drop in target browser usage, lack of new vulnerabilities, efforts to combat domain shadowing (a technique that steals legitimate domain credentials for criminal purposes), cybercriminal arrest, and the ongoing work of developers to improve browsers.
But beyond this scenario, the sudden increase in cryptocurrency miners (which are increasingly valued) cyber crime. Rig EK is falling, but not completely out of the game yet. The researchers noted that the remains of the exploit kit migrated from ransomware distribution to information theft and cryptocurrency miners.
The shift to information theft is not new. In many ways, this is a tendency for exploit kits in general. They were in use before the increase of ransomware - from 2013 - and the distribution of Information Stealers and banking trojans in the early days.
But mining adoption is a new thing for Rig and EKs. Given the trends we have seen, with the sudden surge of coinmining tactics and techniques, this is not surprising. As shown below, mining volume increases by almost 2,800% in one year.
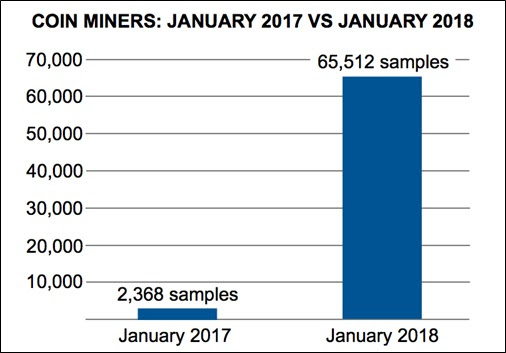
The criminals behind Rig and other EKs have always been focused on maximizing the financial return on their tool investment. And so, we can look at this change of Ransomware back to data theft and in the future for cryptocurrency mining as a possible sign that the era of file hijacking is passing.
We cannot say why this change is happening. There could be a Ransomware change due to a decline in return on investment because people no longer want to pay ransom after the WannaCry / WanaCrypt0r and Petya / NotPetya. Or there may be an effect on the network and attackers are focusing on cryptocurrencies and keeping their distance from ransomware because others are doing the same.
Whatever the reason, the latest declining trends in the Rig EK give us some insight into the global scenario of future threats. The first is that ransomware is finally on its way and the second is that mining of cryptocurrencies It is assuming its role as the main focus for cybercriminals and, therefore, is the threat to which we must focus and greater prevention efforts.



