São Paulo/SP – July 25, 2022. The subject 'Information Security' covers a series of measures and methodologies, such as: policies, process and methods, which aim to guarantee criteria of integrity, confidentiality and availability of data about a company and / or individuals, with the main objective of preserving these data and ensuring that they are only accessed or modified by authorized persons.
*By Edgar Nascimento
The subject 'Information Security' covers a series of measures and methodologies, such as: policies, process and methods, which aim to guarantee criteria of integrity, confidentiality and availability of data about a company and/or individuals, having as main objective the preserving this data and ensuring that it is only accessed or modified by authorized persons.
It is extremely important to keep in mind that the topic does not only concern systems and devices, but also any asset that contains data, examples are:
- People: Company employees have access to a variety of information at work, many of which need to meet the aforementioned criteria, above all, confidentiality.
- Touchable documents: Often, certain departments (an example is in the financial sector of companies) have many printed documents: slips or invoices that, in case of loss, can compromise the availability of information and its confidentiality.
- Environments: There are certain environments within companies where sensitive information is shared, which require complex handling that exudes confidentiality and integrity. As rooms where specific equipment are housed, processes take place or meetings take place, there must be security measures to prevent access by unauthorized persons.
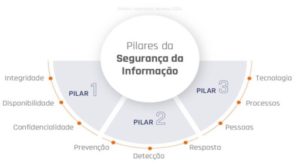
integrity, confidentiality and availability
With this, it is clear that information security refers to how people within an organization use the information they have access to, ranging from a private email or a general report, this data cannot escape the environment. protection, thus making information security a topic beyond a totally strategic issue within organizations: it is a fundamental piece in the functioning of the business and in the current market, more than ever “information is power” and, of course, data play an increasingly strategic role in companies.
According to a Global Information Security Survey carried out in 2018 by “PwC” – 46% of security incidents in Brazil affect company customer information. Another 34%, from its employees. In Brazil, 77% of large companies suffered at least one cyber attack in 12 months.
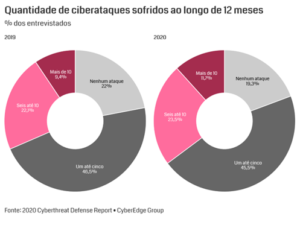
Number of cyber attacks suffered over 12 months
Information security is not just restricted to business data. More than ever, ordinary users who access the internet must also be careful when browsing the net. Exposing sensitive data — whether it's a full name, a document or even which bank you use — is half the battle for fraudsters to pull off identity theft scams.
And with surveys like this, we emphasize the importance of planning and implementing information security measures that involve the entire company to minimize risks and create contingency plans in case of failures or emergency situations. It is no longer so uncommon when looking at the news facing the IT world, we come across companies that have had millionaire losses due to having their systems compromised by a cracker or by some vulnerability that allowed other people to make undue modifications.
The lack of investments and care in these aspects can have serious consequences for companies, causing financial losses, as well as affecting their reputation in the market.
In this sense, it is important that the security area is presented to managers as a priority and strategic investment, capable of generating benefits for the organization.
PREVENTION:
Before investing in infrastructure, the company needs to prepare its internal culture for information security. At this point, for example, it is essential to create and implement policies that reinforce this ideal, instilling in the minds of each employee the relevance of this topic.
A recommended approach to digital security is one that is made up of several layers, capable of preventing any cyberattack.
A combination of firewalls, software and a variety of management tools will help the company fight threats that can affect its systems.
As time passes and information security capabilities become more efficient and comprehensive, so do risks. New malicious software, malware and many other “virtual pests” are created daily to circumvent data security.
Antivirus and firewall are information security tools that complement each other to ensure the availability, confidentiality and integrity of information.
Antivirus is security software against malware and infected programs from the Internet, optical media (DVD and Blu-ray) and the company's internal network, as well as from devices where data was exchanged, such as USB sticks, smartphones and music players. , for example. The firewall, on the other hand, can be considered a protection of computer resources against external threats: it was designed to analyze and filter traffic, ensuring security.
For this, it controls the source and destination IP, source and destination port and protocol flags. In this way, only traffic authorized by it accesses the computer, always in compliance with the pre-established security policy.
Another information security procedure that every company needs to adopt is encryption tools for passwords. Encryption is a security feature that prevents the content of passwords from being accessed by malicious software, hackers, etc.
The greater the variety of characters used in the password, the more difficult it will be to attack. Therefore, try to use passwords with diversified characters, having numbers, capital letters and special characters in their composition.
Technology has been transforming the daily lives of companies, which positively impacts the quality of products and services offered over time. The tools currently available are capable of offering advantages, such as optimizing task time, reducing costs and reducing failures. There are different strategic, operational and practical actions that must be adopted to strengthen information security.
Another important point in the advancement of technology is the improvement in customer relationships. The increase in communication channels contributes to bringing customers closer, as the use of digital tools can also facilitate the resolution of doubts and make the customer more satisfied.
The reality is that no electronic medium is 100% secure, but we currently have cutting edge tools on the market. In addition to several qualified professionals, companies and consulting companies specialized in Information Security, in order for it to be successful, it is necessary to have clear security policies that help to prevent and avoid problems and act on behalf of companies by carrying out tests and providing solutions to the Information Security problems that these companies have, being in 'Compliance', that is, in compliance with rules and laws, brings a series of benefits to the organization, such as, for example, greater market confidence, increased control over risks and reduction of costs and contingencies with fines and negative publicity.
The fact is that, regardless of the business (small or large multinational), it depends on computer systems every day and there is no denying this reality. Without adequate policies to guarantee security, the risks of unwanted access, breach of confidentiality and communications fraud are constant problems.
Information security is certainly one of the most current and most relevant topics in the corporate context, and for this reason, it deserves all the attention of the managers and leaders of a company so that all these measures have real and positive effects, emphasizing the importance in train employees on good practices, as well as use available technological resources.
— Edgar Nascimento is a PL Infrastructure Consultant | SAFEWAY
How can we help?
THE SAFEWAY is an Information Security consulting company recognized by its clients for offering high value-added solutions through projects that fully meet the needs of the business. In 14 years of experience, we have accumulated several successful projects that have earned us credibility and prominence with our clients, who largely make up the 100 largest companies in Brazil.
today through 25 strategic partnerships with global manufacturers and our SOC, SAFEWAY is considered a one stop shopping with the best solutions in technology, processes and people. We have both the technical skills and the experience necessary to assist your company in the process of structuring controls and preparing the environment for the implementation of an ISMS, SGS or SGCN and, consequently, certification of operations, services or companies to the ISO27001, ISO20000 or ISO22301 standards.
In order to support companies in this process of evaluation and adaptation to the requirements of the LGPD, [SAFEWAY] has in its portfolio of services, the Cybersecurity Health Check whose objective is to carry out a diagnosis of the CyberSecurity, Information Security and Data Privacy implemented in your company, contemplating the pillars of Law Suit, People and Technology.
through the Cybersecurity Health Check, risks associated with information security and privacy of internal processes and activities are identified, existing controls and new controls evaluated according to the size of your organization to increase the level of maturity and compliance, in accordance with good information security practices. If you would like more information, contact one of our experts!




