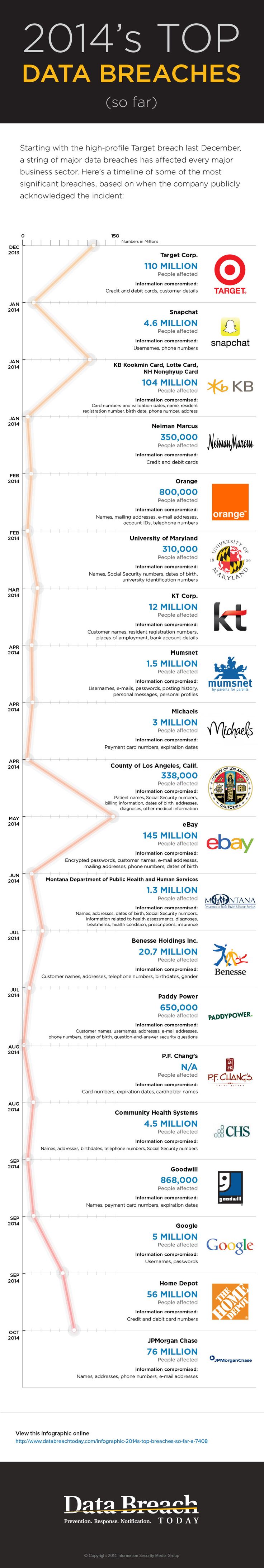
Only one is needed. Only one data breach It is sufficient to have consequences ranging from brand damage, customer friction and regulatory penalties to intellectual property theft and large-scale system vulnerability. To prevent data breaches, you need to employ the most advanced protection provided by a trusted security strategy.
This is why all companies must rely on purchased solutions and security services.
Just a data breach is enough to result in unimaginable damage. Reflect on and answer the questions below:
- Can you proactively respond to all threats?
- Do you know where your confidential data resides?
- Can you enforce IT policies and remedy shortcomings?
- Can you easily manage the lifecycle of your IT assets?
Want to have exclusive content on this topic? Sign up here