São Paulo/SP – January 23, 2023. Cyber Kill Chain it is a cybersecurity model that aims to stage a security attack and then stop the attack before it reaches the last phase, it is a model more focused on intrusion identification and prevention.
*By José Padilha
Cyber Kill Chain, term "Kill Chain” comes from the military environment that identifies and organizes the structure of an attack, when translated into the cyber environment to Kill Chain it helps attackers organize attacks and helps the defending team identify what stage an attacker might be in and how to prevent him from continuing.
what is cyber Kill Chain?
O Cyber Kill Chain it is a cybersecurity model that aims to stage a security attack and then stop the attack before it reaches the last phase, it is a model more focused on intrusion identification and prevention.
Cyber Links Kill Chain
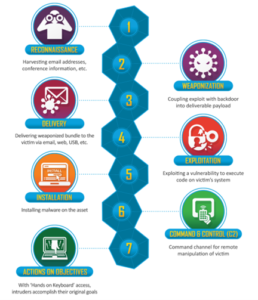
O Cyber Kill Chain It is divided into 7 parts:
1 - Recognition
In this phase the attacker performs a collection of information about the target and raises the tactics to carry out the attack, the attacker can collect the information through information exposed on the internet, through the OSINT (Open source intelligence) or performing direct collections to exposed IPs and websites.
2 - Armament
The attacker begins to organize the tools that will be used to carry out the attack against the targets already found, generally they will be more specific tools that will act in a more discreet way, reducing the chance of being detected.
3 – Delivery
This phase refers to how the attacker will deliver a malicious payload, the most common forms of delivery are those based on human interaction, such as: emails, malicious websites, USB media, among others.
4 – Exploration
After delivering the malicious payload, the attacker will try to elevate his privilege or exploit some other vulnerability he may find locally or on the network in order to gain greater privilege.
5 – Installation
The attacker installs a backdoor so that you can maintain your access within the organization if you lose your initial access, the backdoor can be created through malware.
6 - Command and Control (C2)
In the command and control phase, the attacker installs an agent on the compromised machines, which will connect to an attacker's server, this connection server so that the attacker can send commands and receive their output, this phase differs from the previous one due to the means used, a C2 differs from a simple RAT (Remote Access Trojan) because of its concealment mechanisms and because it is asynchronous, making it even more difficult to identify.
7 – Actions on the objective
The last in this chain is for the attacker to accomplish his objective, be it exfiltration of sensitive data, implementation of ransomware, compromising the integrity of applications made available to third parties, among other things. Phase 7 does not indicate the end of an attack, the attacker can maintain a backdoor in the company for future actions.
Cyber Kill Chain
How to Break the Links Kill Chain?
As mentioned earlier, the model Cyber Kill Chain was created to identify the phase in which the attack is and to stop it, the greater the security maturity, the greater the chances of breaking the link in the chain before the attacker reaches his objectives.
To stop the advance we need to first catalog the controls and their functions:
- To detect – Controls that will identify the attack.
- Denial – Controls that will block the attack when it occurs.
- Interrupt – The controls will interrupt the attacker's communication.
- Degrade – The controls will disrupt the attacker's communication with the systems and then interrupt them in order to simulate a overflow in communication preventing the attacker from taking anti-defense actions.
- Trick – The controls will deceive the attacker with false information, for example they will make intentionally infected systems available to be exploited and thus the presence of the attacker on the network is detected.
- To contain – The controls will contain the attack to a part of the network or organization, so as to limit the attacker's access.
Below are some of the ways to identify and prevent the current from advancing:
- Recognition:
- Detect: IDS Systems, Data Monitoring Logs;
- Negation: WAF (Web Application Firewall), IPS;
- Trick: Port Sentry, honeypot.
- Armament
- Detect: IDS, Log Monitoring;
- Denial: IPS, EDR, Spam Filters.
- Delivery
- Detect: IDS;
- Denial: IPS, EDR.
- Exploration
- Detect: IDS, HIDS;
- Denial: IPS, EDR.
- Installation
- Detect: HIDS;
- Denial: HIPS, EDR.
- Command and Control (C2)
- Detect: IDS, HIDS, Monitoring logs.
- Denial: IPS, HIPS, EDR;
- Interrupt:
- Actions on the goal
- Detect: IDS, HIDS, Monitoring logs;
- Deny: IPS, HIPS, EDR, Data-at-Rest Encryption;
- Trick: honeypot;
- Interrupt: Firewall.
— José Padilha is Full Pentester at [SAFEWAY]
How can we help?
THE SAFEWAY is an Information Security consulting company recognized by its clients for offering high value-added solutions through projects that fully meet the needs of the business. In 14 years of experience, we have accumulated several successful projects that have earned us credibility and prominence with our clients, who largely make up the 100 largest companies in Brazil.
today through 25 strategic partnerships with global manufacturers and our SOC, SAFEWAY is considered a one stop shopping with the best solutions in technology, processes and people. We have both the technical skills and the experience necessary to assist your company in the process of structuring controls and preparing the environment for the implementation of an ISMS, SGS or SGCN and, consequently, certification of operations, services or companies to the ISO27001, ISO20000 or ISO22301 standards.
In order to support companies in this process of evaluation and adaptation to the requirements of the LGPD, [SAFEWAY] has in its portfolio of services, the Cybersecurity Health Check whose objective is to carry out a diagnosis of the CyberSecurity, Information Security and Data Privacy implemented in your company, contemplating the pillars of Law Suit, People and Technology.
through the Cybersecurity Health Check, risks associated with information security and privacy of internal processes and activities are identified, existing controls and new controls evaluated according to the size of your organization to increase the level of maturity and compliance, in accordance with good information security practices. If you would like more information, contact one of our experts!